About Intel Management Engine (Intel ME) & Intel Active Management Technlogy (iAMT)
Tags: intel me, intel amt
Last update: Jun 2018
Technological overview
The Intel Management Engine (Intel ME) is a standalone microcontroller component which operates independent from your computer’s hardware. It provides an interface between operating system, hardware and BIOS. The Intel ME subsystem is hosting the firmware of Intel Active Management Technology (iAMT). Intel ME and iAMT has been developed for so called out-of-band managebility: remote administration of computer systems.
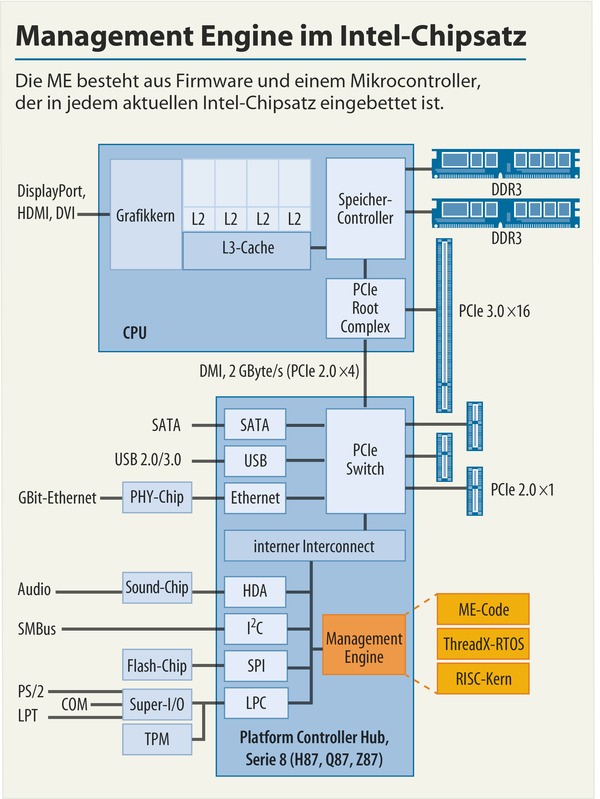
The Management Engine (yellow) has a separated connetion to the internal Interconnect; allowing the Intel ME core processor (RISC core) to bypass other subsystems like TPM and SMBus. To bypass every piece of software running on your computer you can think of. (Source #02)
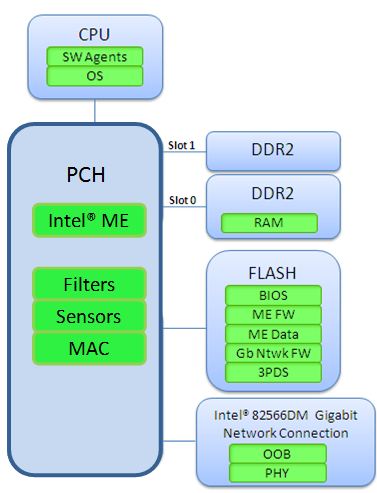
The Intel AMT is stored in a flash memory and protected against unauthorized access. On PC’s power-up the firmware is going to be uploaded into the RAM. Afterwards Intel ME executes this uploaded (iAMT) firmware and those allows the CPU to reset in order to initiate the whole boot process and to load the operating systems kernel etc.
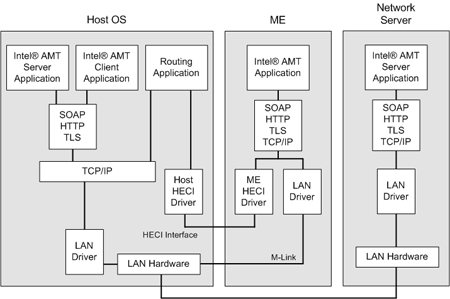
The Intel ME is directly connected to the LAN hardware through a builtin driver. This allows the ME to communicate secretly via LAN, WLAN and mobile networks while bypassing the operating system (Source #08). Until now there has been no discovery of suspicious network packets which does not necessarily mean that it could not.
Short conclusion
In other words: Your computer is running Intel ME all the time. Invisible. Even if the PC is powered off.
Is there a problem?
People who are keen on security and try to avoid risks are noticing it immediately: If there is an underlying second operating system – do we have control over it? How secure is this at all? Is there a way to disable Intel ME and Intel AMT?
To Answer those questions we need to check out if there is a sufficient documentation out there which allows to comprehend all mechanisms and we need to watch out for possible security flaws.
Documentation
There is an Intel AMT Implementation and Reference Guide out there. It describes the Intel AMT features and how to use the SDK. There is a short passage about how to enable or disable the “Intel AMT Network”. At least some OEM vendors allow to disable iAMT in the BIOS settings (source #04).
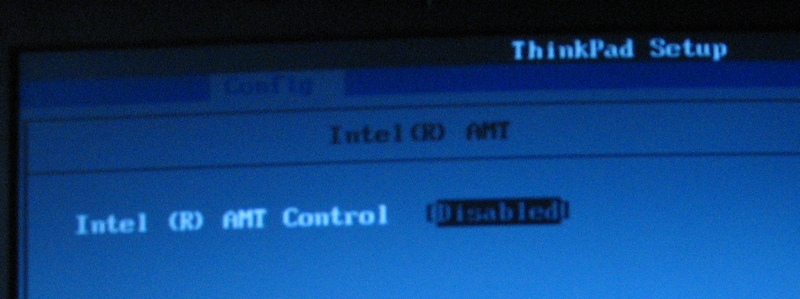
The Intel ME BIOS Extension can be accessed through CTRL+P during bootup. The default password is “admin”. There is a User Guide for the Intel ME BIOS Extension but there is no option for disabling Intel ME – just changing some parameters and configuring the iAMT.
That means the status of the underlying Intel ME can’t be changed. There is no source code availabe and according Intel will never be. Usually there are two reasons for that: The code is entirely kept secret due to the ownership of intellectual property – or the code doesn’t belong to Intel at all. In fact scientists found out recently, that the Intel ME firmware seems to be based on Andrew S. Tanenbaum’s Minix (source #06), which has been released under BSD license.
So as far as we know the Intel ME can’t be disabled at all. In addition there is no documentation available. We can draw the conclustion that nobody knows how this subsystem operates. As a matter of fact we have no control over it and are not able to influence its behaviour. In cybersecurity terms such a thing is called a blackbox and there is only one way to find out more about it: investigative testing.
Security vulnerabilities and exploits
Please refer to a list of known vulnerabilities to get a more detailed picture about Intel ME’s security. Just to mention some of them:
- Ring-3 rootkit
- Zero-touch provisioning
- SA-00075/ Silent Bob is Silent
- PLATINUM
- SA-00086
This management engine is definitely running. The lack of an ordinary documentation leads inevitable to security holes which represent a not only potentional but and proven risk to data and computer security.
What is affected?
The Intel ME is integrated into all intel desktop, mobile and server systems since June 2006. It has been launched with the “Intel 965 Express Family” and the “ICH8 I/O Controller Family” (source #09).
Is there a solution?
Vendor updates
There is no known method to fix vulnerabilities except updating the Intel ME firmware by the vendor/oem. However, an attacker with access to the ME firmware is still able to flash an old vulnerable version in order to use an exploit.
Trying to deactivate Intel ME
Russian researchers analyzed Intel ME v11 and discovered a special operations mode called High Assurance Platform (HAP). Once this bit is set it disables some parts of the engine in an early state. Unfortunately it’s not possible to disable or erase all parts of Intel ME since some part of the ME firmware is checking Intel’s signatures, which are hardcoded within the hardware. Only if this check completes successfully the hardware is allowed to boot up. There is a software called ME Cleaner to get rid of some parts of the Intel ME firmware.
Buying current hardware with Intel ME (probably) disabled
The following vendors are currently providing almost “clean” hardware. It’s unknown and unsure if the Intel ME is really deactivated.
- Purism sells security and privacy focused hardware while using ME Cleaner
- Dell ships “Latitude 14 Rugged” notebooks on custom order with “No Out-of-Band Management”
Buying old hardware where Intel ME hasn’t been implemented yet
The much better option is to use a device which has no Intel ME at all. Please refer to CPU and system alternatives without Intel ME iAMT and AMD PSP / Secure Technology.
Sources
- Figure 1: heise.de [DE]
- Figure 2: intel.com [EN]
- Figure 3: heise.de [DE]
- Source 01: Wikipedia Intel Active Management Technology [DE]
- Source 02: Heise: Wandelbare Verwaltungsmaschine [DE]
- Source 03: Intel AMT and the Intel ME Software [EN]
- Source 04: Intel Business Client Software Develeopment Forum [EN]
- Source 05: Hackaday Neutralizing Intels Management Engine [EN]
- Source 06: Tanenbaum Minix [DE]
- Source 07: Wikipedia Intel Management Engine [EN]
- Source 08: Spekulationen um geheime Hintertüren [DE]
- Source 09: Libreboot [EN]
- Source 10: Intel ME weitgehend abschaltbar [DE]
- Source 11: Heise Dell schaltet Intel ME in Spezialnotebooks ab [DE]
- Source 12: Disabling Intel ME 11 via undocumented mode [EN]

Leave a Reply
Want to join the discussion?Feel free to contribute!