How to build a more secure personal computer
Tags: Coreboot, F2A85-M, F2A85-M PRO, A10-5800K
Last Update: Jan 2021
This guide is based on the BIOS UEFI replacement called Coreboot which runs on an ASUS F2A85-M or F2A85-M PRO mainboard with an AMD A10-5800K CPU with integrated graphics.

1. Introduction and aim
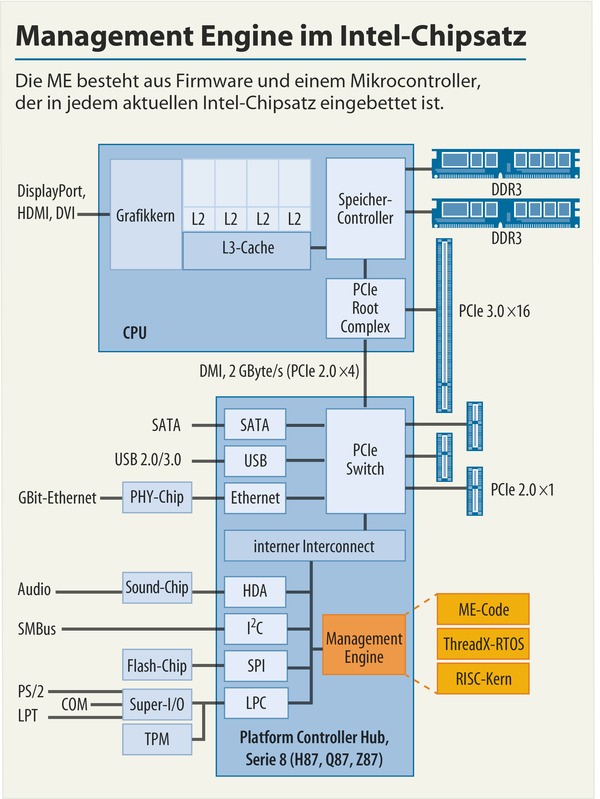
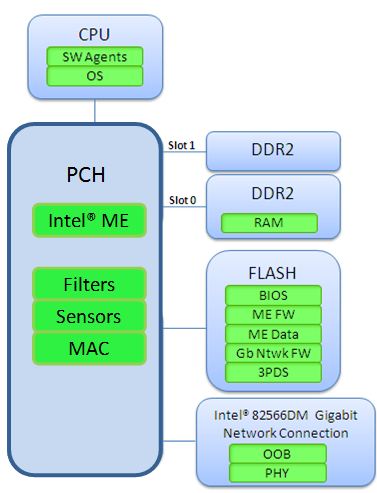
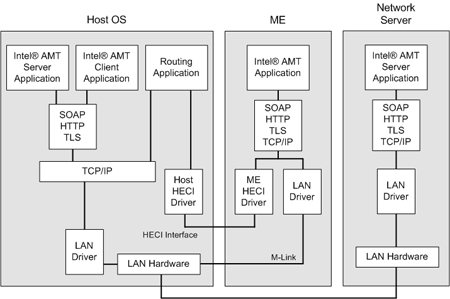
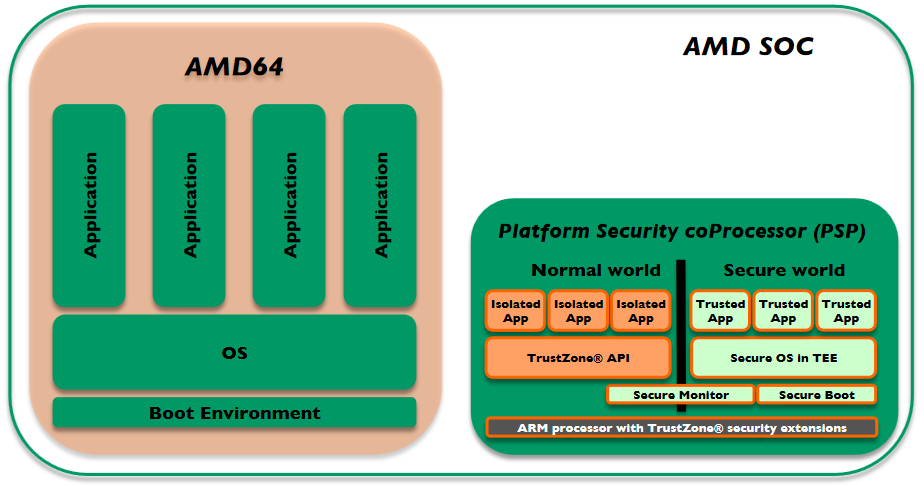
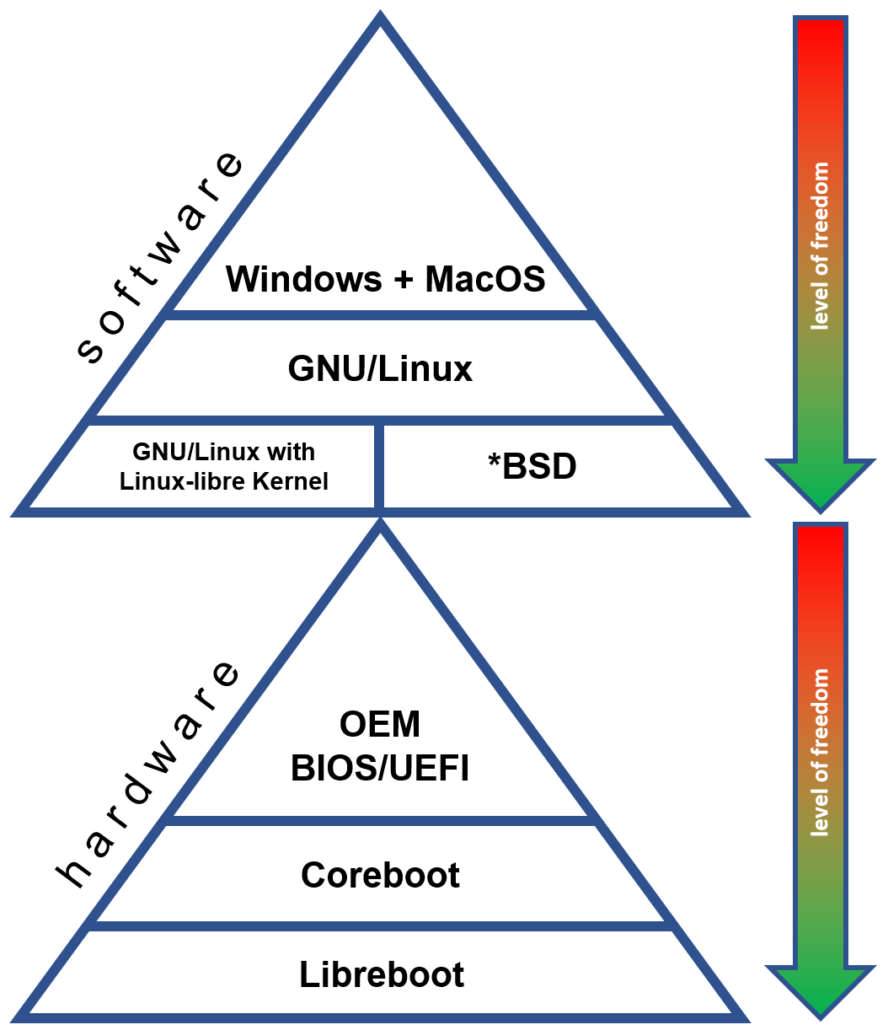
This initial idea came up with the uprising problems and vulnerabilities of Intel ME and AMD Secure Technology (PSP). After having researched several alternatives without running those (in)secure technologies I was looking for very specific hardware to meet the requirements on security as mentioned in the pinetree of open and secure classical computing.
The aim is to provide a comprehensive guide which allows the daily user to gain a higher level of security. The daily user shall be empowered to get back the control about every piece of hardware within the computer system. In general hardware is always run by the so-called firmware. Firmware is software which is in the closest control of the underlying hardware to make it work as intended. So firmware is needed by the all BIOS/UEFI computer systems we know. Based on these hardware firmwares the central BIOS/UEFI unit is able to tell other computer parts how to cooperate. The newer the hardware, the worse the availability of open firmware. In fact in most cases the availability of open code is zero, because vendors assume that keeping the source code secret (closed source code) increases the security of the product. Nowadays we’ve learned by many lessons that this conviction is wrong. It’s a fact that every source contains errors which might be exploitable if they are found. The more people access a source code, the better this code is reviewed and the fewer errors are included.
Conclusion: Due to this circumstance sometimes developers have to use vendor’s original binary code (firmware) to get the hardware to work at all. That means that wide limitations are accepted by almost all vendors. Security can only be guaranteed by open source code. This leads to a conflict of objectives: On one hand we want a secure system and on the other hand we don’t want to lose comfort by leaving out the functionality which the vendor has placed within his (closed) firmware.
Maybe you take this into account before you support a certain vendor by buying his hardware the next time.
Since it’s practically almost impossible to use every piece of hardware out there by open code, we need to find the best compromise between functionality and security:
- free and open source code
- running Coreboot or even Libreboot
- running Windows and GNU/Linux
- as little as possible of (closed) firmware
- enough performance to get work done
2. Software we will need
- For booting the system we will use Coreboot instead of the vendor’s BIOS/UEFI. Libreboot is even a “better” option but – as mentioned in other posts – unfortunately very few and old boards are supported.
- As an operating system you can choose one from the recommendations. I prefer using Manjaro GNU/Linux with the free driver stack option which you can choose while booting the installation disk from a pen-drive. In my view this is the best mix between bleeding edge development, security and user comfort.
- If you prefer to build the Coreboot ROM on your own, you need a Linux on which you can compile the Coreboot sources. Ubuntu is usually a good choice.
- If you prefer to extract the VGA BIOS on your own, you will also need to run a live Linux from a pen-drive for extraction.
3. Hardware you will need (mostly second hand)
| Hardware used | Notes | $ |
|---|---|---|
| Mainboard F2A85-M PRO 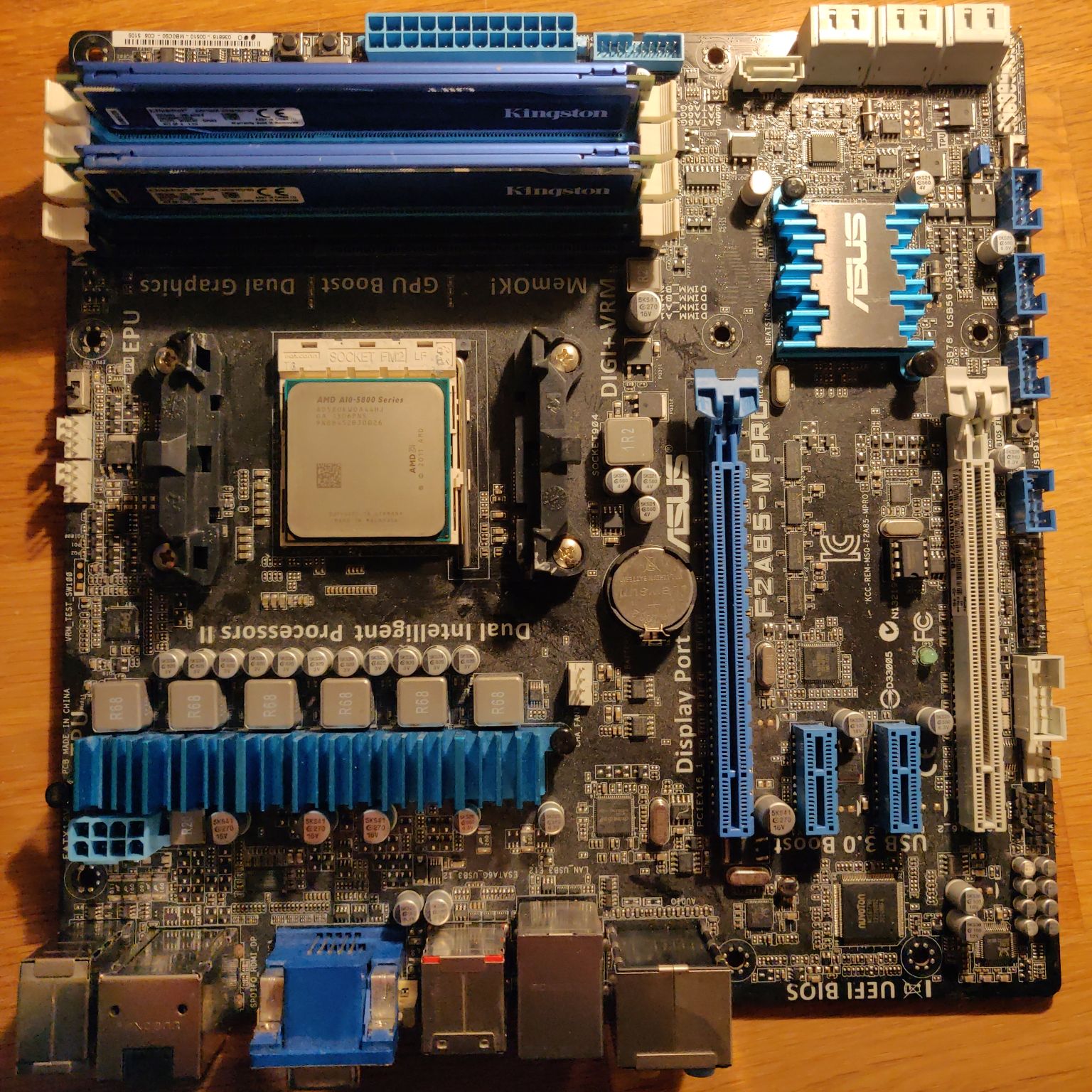 | Both the ASUS F2A85-M or F2A85-M PRO are currently the best choice for a desktop platform, because it is widely supported by Coreboot. | 40 |
| CPU AMD A10-5800K  | As we found out before AMD’s Piledriver and Steamroller CPU architectures (codenames Trinity, Richland and Kaveri) are the latest ones which does NOT include those (in)secure technologies. The AMD A10-5800K or AMD A10-6800K are the most compatible and powerful CPU/APU you can run on with Coreboot on this mainboard. | 40 |
| CPU Cooler Xilence A250PWM  | Pick any adequate CPU cooler you want which is supporting the FM2 socket. You can use a good old Arctic Freezer A30 with a silent 120mm fan (~ 30 $). If you want something new you can take the Xilence A250PWM (XC035). | 10 |
| Memory Kingston KHX1600C10D3B1K2 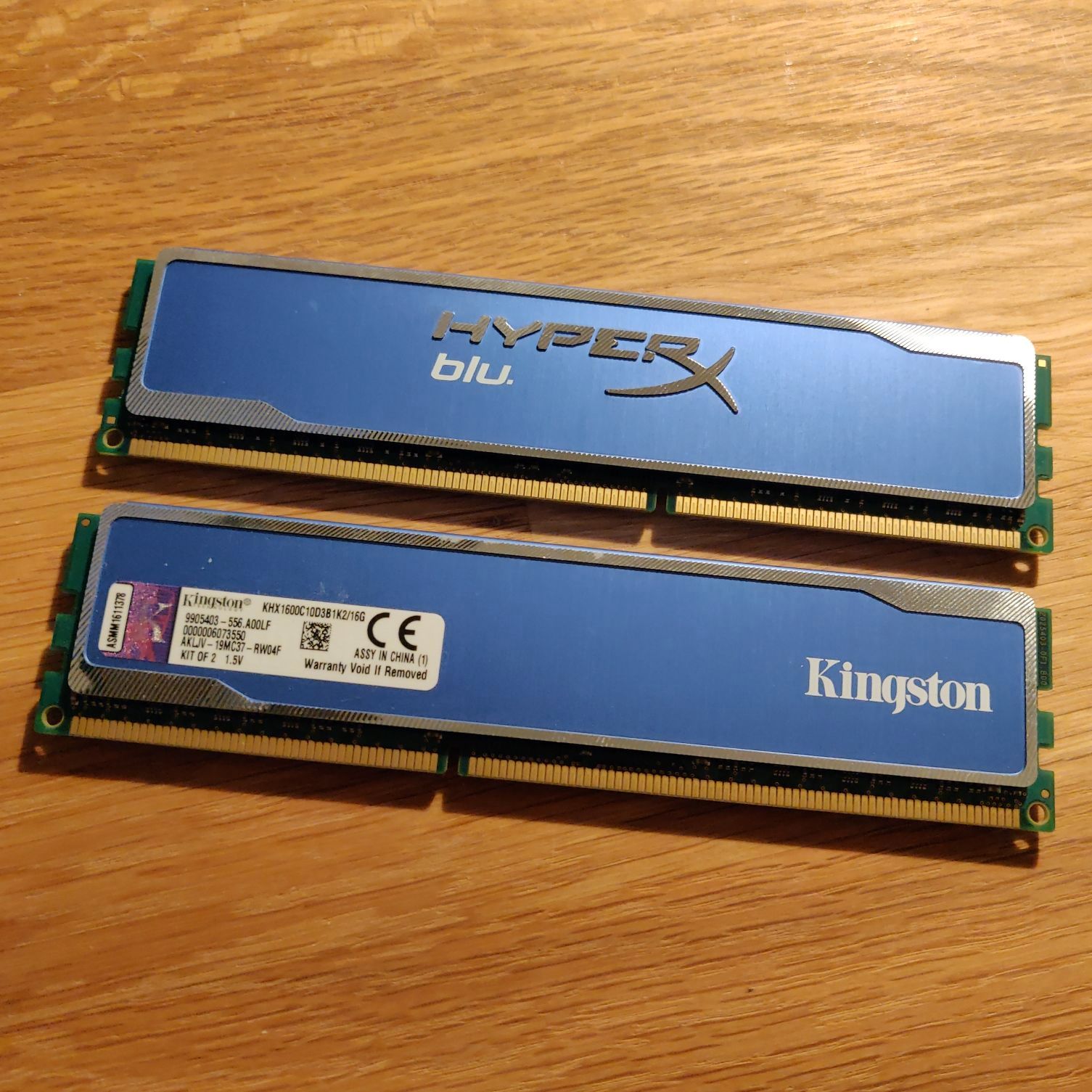 | DDR3-1866 RAM is the fastest RAM speed our CPU is supporting. The amount depends just on your personal demands. With a minimum of 8 GB we should be good to go. I’ve been successful with Corsair CML16GX3M2A1600C100 and Kingston KHX1600C10D3B1K2; but there are many many others that will work, too. | 50 |
| HDD/SSD | We need a SATA hard-drive for the operating system. Think about using a SSD if you want a fast system. Remember to encrypt your partitions and/or files – especially if you are using a SSD. | 50 |
| GPU | In the CPU above the graphics are onboard and included within the CPU. So there is no need to buy a dedicated one. | 0 |
| Power Supply | As a power supply any standard ATX AC adaptor will work. | 30 |
| Case Bitfenix Prodigy M  | Choose a computer case according to your personal preferences. I like the Bitfenix Prodigy M. Remember: Not all micro ATX cases are suitable for taking bigger/higher CPU coolers. This one takes and bigger CPU cooler like the Freezer A30 perfectly. | 50 |
| Flashtool CH341A  | In order to flash the BIOS chip via SPI we need a CH341A USB Programmer. | 15 |
| BIOS chip W25Q64FVAIG 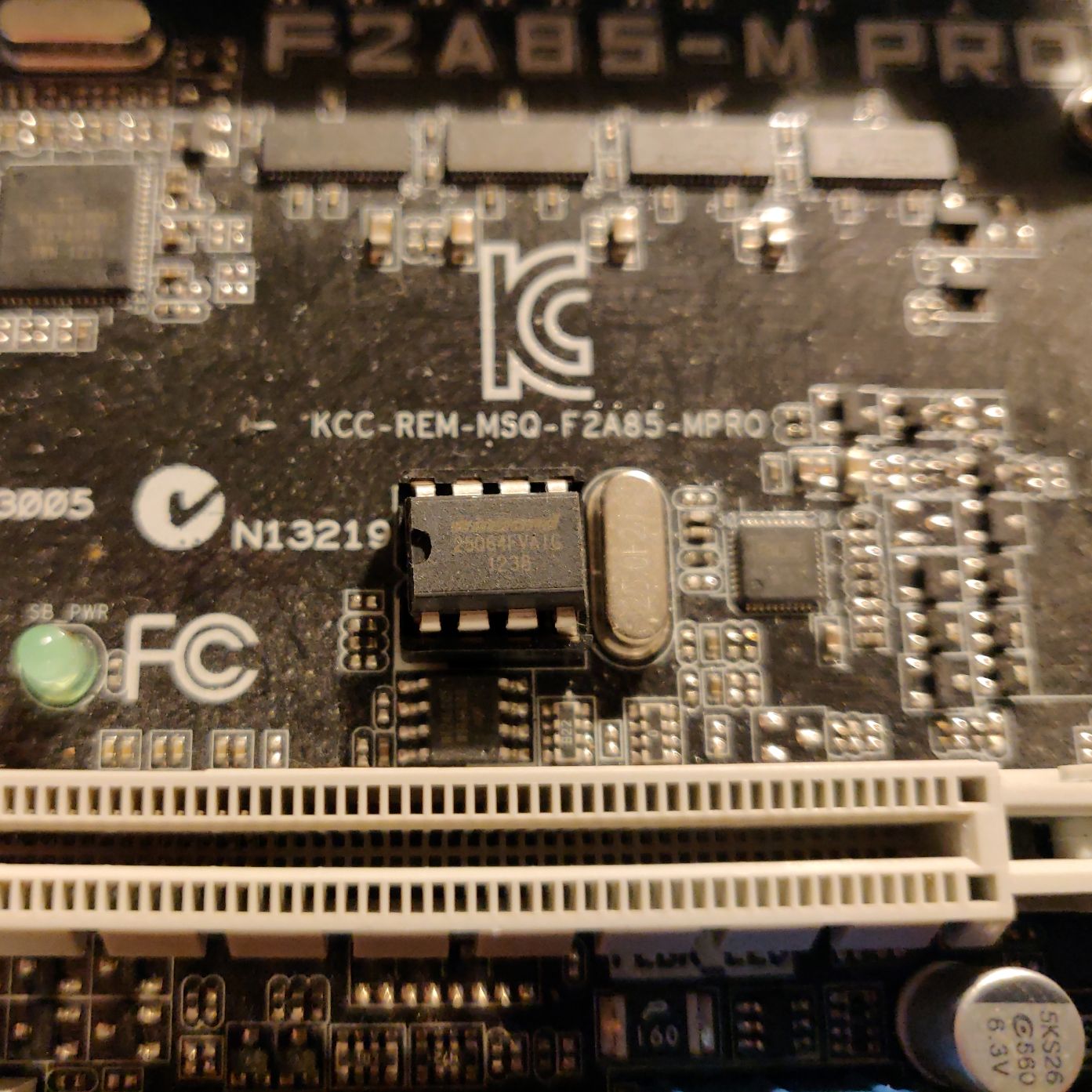 | I recommend strongly to buy a separate Winbond W25Q64FVAIG or W25Q64BVAIG spare chip in order to flash the Coreboot build onto it. There are people who flash the onboard chip during a running system but this process can fail and in my opinion it’s better to have a fallback – just in case flashing or extraction have failed. | 10 |
| total cost, approx. | 295 |
4. Assembling your computer
I assume you know how to assemble a computer so now it’s a good time to do so. Make sure your DDR3 RAM is placed into the BLUE SLOTS. Otherwise your computer won’t boot up.
5. Extracting the VGA BIOS binary blob
Unfortunately the internal GPU won’t work unless we integrate its binary into the Coreboot ROM.
You can download now the vgabios.zip which contains the vgabios.bin which I have extracted already from an AMD A10-5800K. Or you download it on your own following the Coreboot guide:
Boot up a linux live Distro like Ubuntu from your prepared pendrive.
Check the ID by issueing “lspci -tvnn”. As you can see my ID of the GPU is 1002:9901. Write the ID down. We will need it later to build the Coreboot ROM.
lspci -tvnn
-[0000:00]-+-00.0 Advanced Micro Devices, Inc. [AMD] Family 15h (Models 10h-1fh) Processor Root Complex [1022:1410]
+-00.2 Advanced Micro Devices, Inc. [AMD] Family 15h (Models 10h-1fh) I/O Memory Management Unit [1022:1419]
+-01.0 Advanced Micro Devices, Inc. [AMD/ATI] Trinity [Radeon HD 7660D] [1002:9901]
+-01.1 Advanced Micro Devices, Inc. [AMD/ATI] Trinity HDMI Audio Controller [1002:9902]
...For enabling to read the ROM we need to set a enablement bit 1 to the corresponding address 0000:00:01.0 which we found above:
echo 1 > /sys/devices/pci0000:00/0000:00:01.0/romNow we can extract the VGA BIOS into a binary. Copy the vgabios.bin file onto a pendrive.
cp /sys/devices/pci0000:00/0000:00:01.0/rom vgabios.bin6. Building the Coreboot ROM
If you want to skip this step or encounter unsolvable errors prohibiting you to generate the ROM you can download one of my compiled ROMs:
- coreboot.rom for AMD A10-5800K & ASUS F2A85M-PRO
- coreboot.rom for AMD A10-5800K & ASUS F2A85M (coming soon)
Since the old method isn’t working anymore you can decide now if you want to prepare Ubuntu Linux on your own or want to download my already prepared Virtual Machine I prepared for you.
6a. Preparing Ubuntu 20.04 LTS for building Coreboot
Get yourself a fresh copy of Ubuntu 20.04 LTS. Supply your Ubuntu with needed packages:
sudo apt-get install git build-essential gnat flex bison libncurses5-dev wget zlib1g-dev pythonLet’s clone the Coreboot repository and change into that folder:
git clone https://review.coreboot.org/coreboot
cd corebootNow copy your vgabios.bin from chapter 5 into the root directory of your Coreboot folder. Alternatively you can use my extracted vgabios.bin from a 5800K:
wget https:/freundschafter.com/download/coreboot/vgabios.binNow you can set up the Coreboot environment for building the Coreboot ROM, which we’ll transfer to our BIOS chip.
6b. Setup your settings for the Coreboot build
Run the configuration wizard with:
make nconfig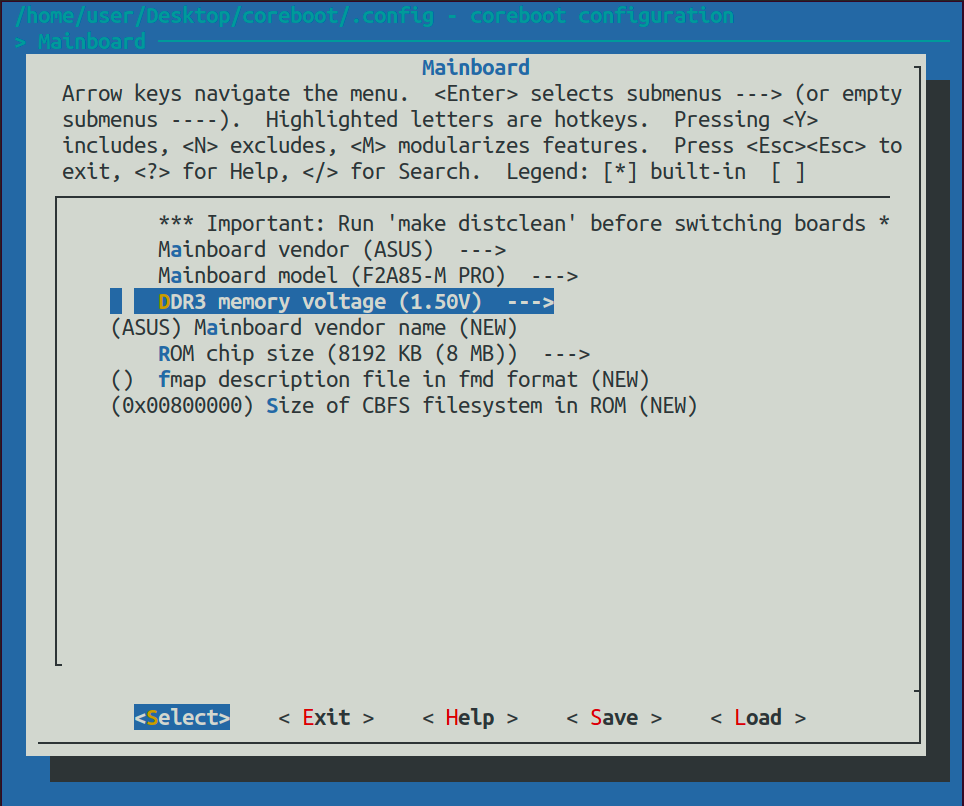
Set up the following parameters:
- Submenu Mainboard: Choose ASUS as vendor.
- Submenu Mainboard: Choose F2A85-M or F2A85-M PRO as model.
- Submenu Mainboard: Choose the DDR3 memory voltage. Refer to your vendor’s website if you are unsure. Possible values are 1.35 / 1.5 / 1.65 V. Some tester said 1.5 V is the failsafe value if you can’t figure it out.
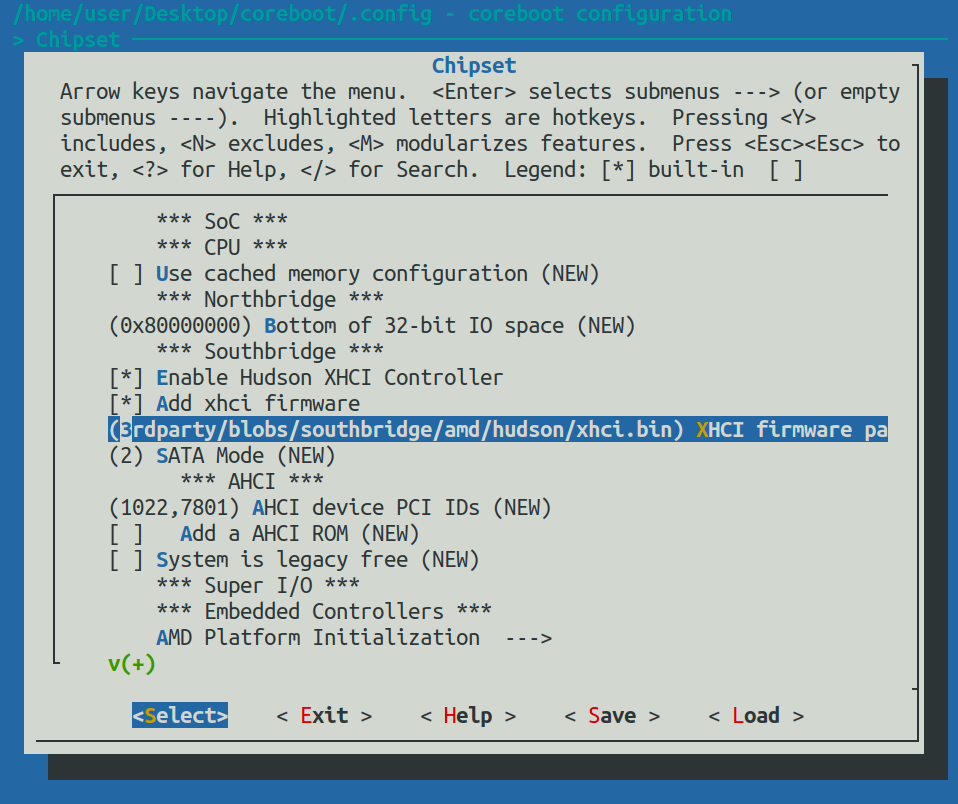
- Submenu Chipset: Enable Hudson XHCI Controller
- Submenu Chipset: Add XHCI firmware. The default path is already set correctly.
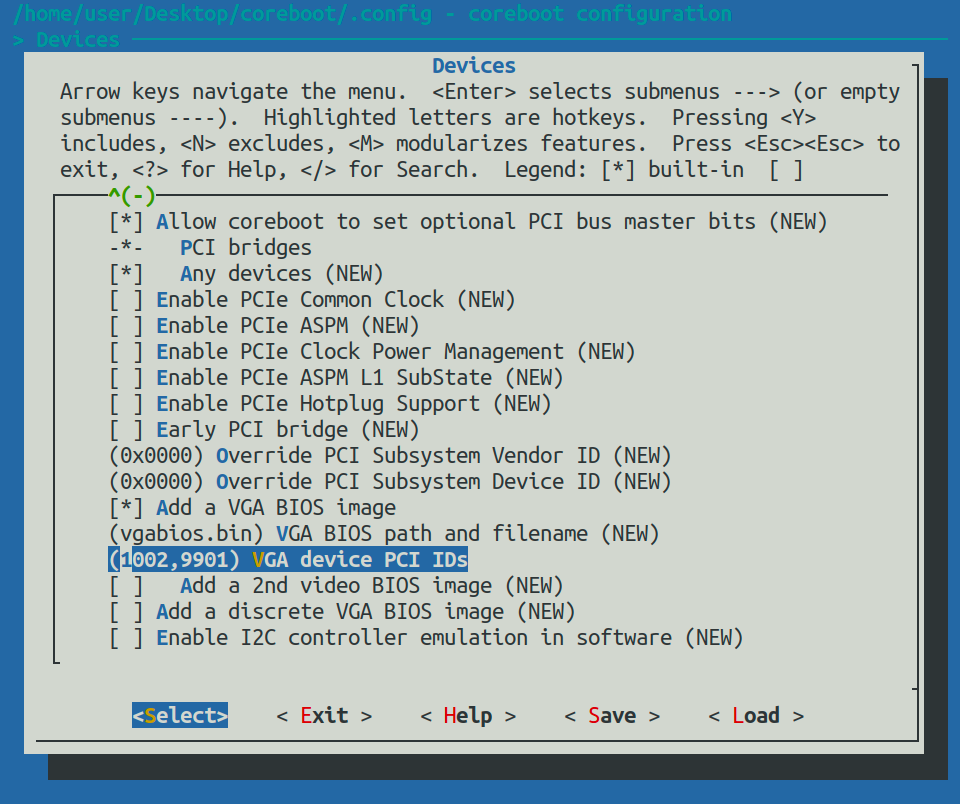
- Submenu Devices: Add your VGA BIOS image (your extracted one, or mine) and make sure the PCI ID is matching yours by typing in the right values. For our CPU 5800K the value is always the same: 1002,9901.
Save your configuration by hitting “Save”, leave the filename “.config” and exit the tool.
Build the Compiler. CPUS=4 means it will use 4 cores to compile. Adjust this value to meet your number of cores. Be patient, this process takes some time. With my older notebook I had to wait around 10-20 minutes.
make crossgcc-i386 CPUS=4Finally we are able to build the Coreboot ROM:
makeYou will find the generated coreboot.rom in a subfolder called build.
7. Flashing the Coreboot ROM
- Place your spare chip on the USB programmer and plug it into a USB port on your Linux machine.
- Install flashrom under Ubuntu by
sudo apt-get install flashromFlash your spare chip now with your generated coreboot.rom:
sudo flashrom -n -w build/coreboot.rom --programmer ch341a_spiIf you get the following notifications your chip is ready:
Found Winbond flash chip "W25Q64.V" (8192 kB, SPI).
Erase/write done.
Verifying flash... VERIFIED.Replace your old BIOS chip by the new flashed one during your system is switched off. Be careful not to bend a pin. So-called DIP8 pliers might help you to release the chip from the board.
Just in case you mess something up you can download a fresh vendor’s copy of the original BIOS/UEFI image and flash it again:
8. Operating System
Now, equipped with Coreboot, you can choose to install any operating system you wish. Since I am very familiar with it I’d go with something Debian-based: PureOS. If you want to follow me, you’ll notice that after installation of PureOS 9.x your screen will remain black due to the lack of AMD graphics firmware packages within PureOS. (Actually it’s a good sign because now you see that binary blobs like the AMD firmware really weren’t loaded during bootup). To fix this we need to install a package into our PureOS installation:
8a. Prepare the pendrive
Get a pendrive formatted with FAT and use another computer to prepare it. Download the firmware.zip archive from https://cdimage.debian.org/cdimage/unofficial/non-free/firmware/testing/current/ and extract firmware-amd-graphics*.deb from it. If you use Linux you can use the following lines:
wget https://cdimage.debian.org/cdimage/unofficial/non-free/firmware/testing/current/firmware.zip
unzip firmware.zip firmware-amd-graphics*.debCopy this .deb package into your pendrive, unmount it and plug it into your secure computer system.
8b. Installing the AMD graphics firmware
First login into the system on another TTY by pressing Crtl + Alt + F3 by providing your user and password. Afterwards we will create a new folder as mounting point for your pendrive, mount it, and install the .deb package. You will need the identifier for your pendrive partition. You can find it out by using “lsblk” for instance. In my case it’s /dev/sdb1.
sudo mkdir /pendrive
sudo mount /dev/sbd1 /pendrive
cd /pendrive
sudo apt install ./fireware-amd-graphics*.deb
cd /
sudo umount /dev/sdb1After having installed the graphics firmware you can now unplug your pendrive, reboot your system by issuing “reboot” and enjoy PureOS welcoming you.