How to inspect network traffic on your cell phone / mobile device
Tags: analyze traffic, mobile traffic investigation, mitm proxy attack
Last update: Feb 2021
Foreword
In this tutorial we will use a regular computer with two USB wifi adapters: one for the connection to our internet/wan and the other one for creating our local wifi hotspot. You can substitute one of the wifi adapters with an ethernet adapter of course. I’m using two wifi adapter in order to not mess around with cables and because they were laying on my shelf. Pretty all others should work, too.
1. Used hardware / software
- some computer with Ubuntu 20.04 LTS installed (Linux Mint also worked)
- usb wifi adapter #1: TP-Link TL-WN321G (chipset RT2501/2573)
- usb wifi adapter #2: TP-Link TL-WN722N (chipset AR9271)
- you’ll need to install the proxy tool:
sudo apt-get install mitmproxy
2. Setting up the wifi adapters
I’m using Ubuntu or Mint for this first steps because it’s quite easy to set it up with GUI’s. For other distributions this way might differ a bit.
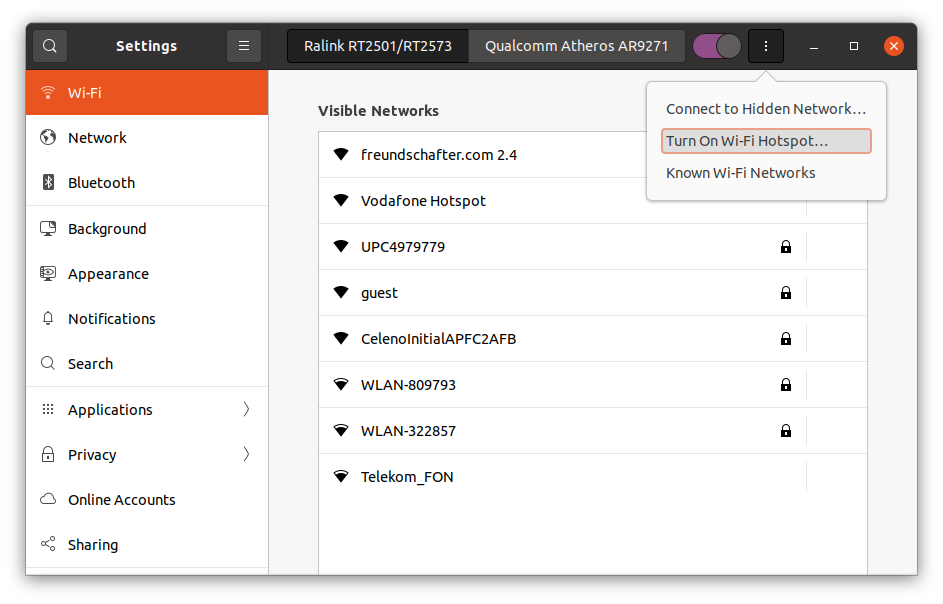
Turn on the wifi hotspot for the first wifi adapter.
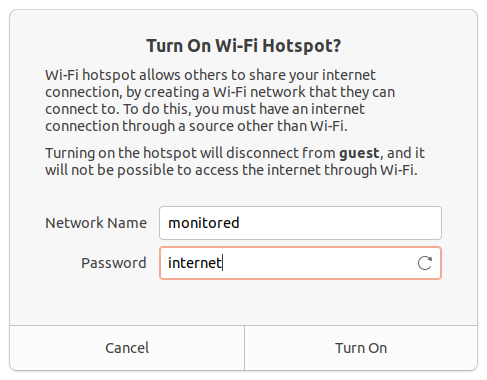
For the sake of this tutorial we’ll keep things easy and use “monitored” as SSID and “internet” as password.
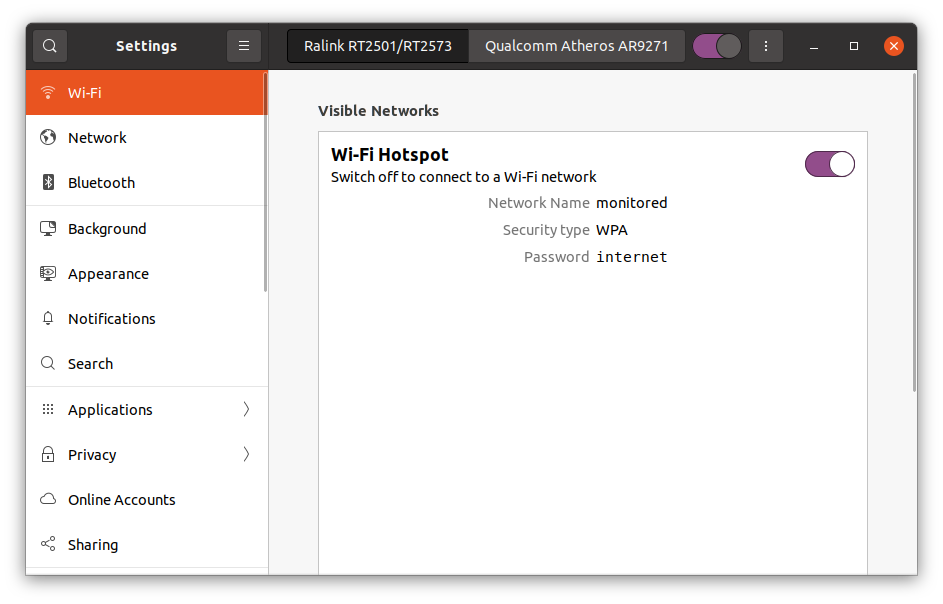
You should see something like this in the end.
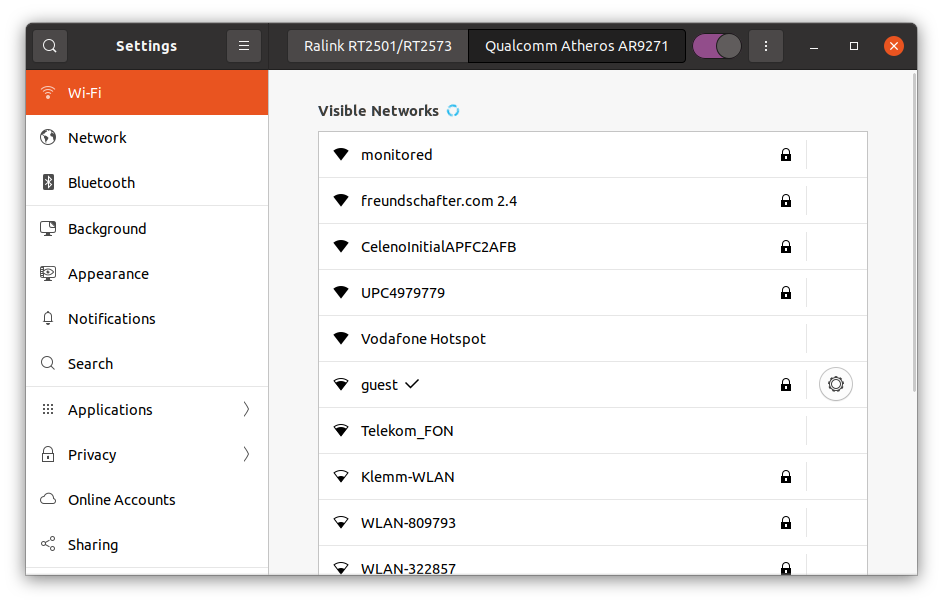
The second adapter will be connected with the internet/wan. Namely called “guest”.
3. Checking the connections and parameters
It’s important to check the output of “ifconfig” just to make sure everything has been set up correctly.
wlx6470022a323f: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.179.68 netmask 255.255.255.0 broadcast 192.168.179.255
inet6 fe80::1927:4d17:ceef:b47a prefixlen 64 scopeid 0x20<link>
ether 64:70:02:2a:32:3f txqueuelen 1000 (Ethernet)
RX packets 6106 bytes 6409739 (6.4 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4896 bytes 1197861 (1.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlx940c6de46be3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.42.0.1 netmask 255.255.255.0 broadcast 10.42.0.255
inet6 fe80::d6fe:b25f:3863:244e prefixlen 64 scopeid 0x20<link>
ether 94:0c:6d:e4:6b:e3 txqueuelen 1000 (Ethernet)
RX packets 183 bytes 27080 (27.0 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 384 bytes 60515 (60.5 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0What do you learn from this console output? Several important things:
- wifi adapter #1 is accessible by its name “wlx6470022a323f”
- wifi adapter #1 owns the local IP 192.168.179.68 from the guest-testing network with access to the internet
- wifi adapter #2 is accessible by its name “wlx940c6de46be3”
- wifi adapter #2 own a local IP 10.42.0.1 without any further access right now
4. Enabling routing and setting up the firewall rules
Now we need to enable IP forwarding.
sudo sysctl -w net.ipv4.ip_forward=1And add some firewall rules for wifi adapter #1: wlx6470022a323f
sudo iptables -t nat -A PREROUTING -i wlx6470022a323f -p tcp --dport 80 -j REDIRECT --to-port 8080
sudo iptables -t nat -A PREROUTING -i wlx6470022a323f -p tcp --dport 443 -j REDIRECT --to-port 8080Afterwards we need some additional rules for wifi adapter #2: wlx940c6de46be3
sudo iptables -t nat -A PREROUTING -i wlx940c6de46be3 -p tcp --dport 80 -j REDIRECT --to-port 8080
sudo iptables -t nat -A PREROUTING -i wlx940c6de46be3 -p tcp --dport 443 -j REDIRECT --to-port 80805. Starting mitmproxy
In order to be able to watch the traffic you need to start the sniffing host/proxy.
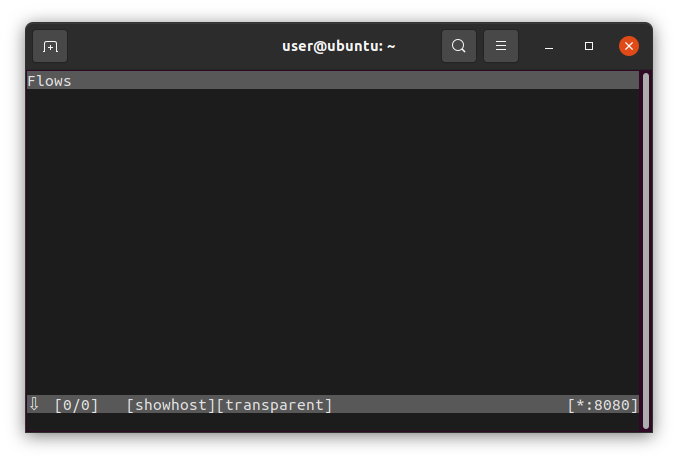
Start the proxy with: mitmproxy --mode transparent --showhost
You’ll find an empty window because no device is connected with our hotspot named “monitored”.
6. Connect with a mobile phone
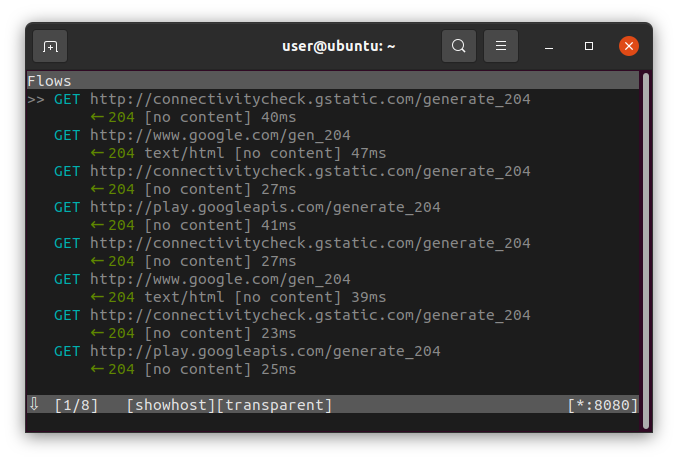
Take your mobile phone and connect to our hotspot “monitored”. As soon as we connect, the network traffic should be visible. Is this case we can see some default Android behavior.
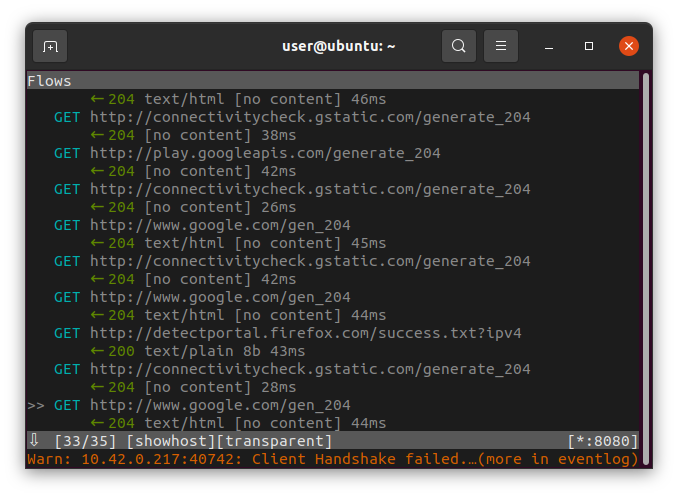
If you try to connect to an encrypted website on your mobile phone, you’ll get some error message at the bottom, that a (TLS) Client Handshake failed. In order to make this encryption visible we need to install an intermediate encryption certificate on our phone which is provided by our tool mitmproxy: Open up the browser on your phone and open the website “mitm.it”. You’ll be redirected automatically to a page where you can choose to download and install the certificate (depending on your device).

Leave a Reply
Want to join the discussion?Feel free to contribute!